
Rome wasn’t built in a day and the same is true of a good Identity and Access Management (IAM) programme. When planning your IAM priorities for maximum business value, you need to consider the below points:
Time & money
IAM projects take a significant investment of time and finances and if you don’t have the right support along the way, often more than planned. It's important to accept before you begin planning that delivering IAM business change is a marathon, not a sprint. Don’t believe the sales pitch that choosing the right tool will solve all your problems overnight!
Return on investment
IAM should be considered a product or value stream, where value is delivered iteratively over time, rather than a project with a defined end. Agree what milestones and success factors the stakeholders value upfront. These milestones will likely change over time, but ensuring all parties understand that value will be delivered iteratively and won't solve all your problems overnight, will avoid difficult conversations further down the line.
Your particular challenges
Focus on why you're undertaking and developing an IAM strategy and what your key drivers are. Balance immediate challenges with strategic objectives; but beware, the immediate challenges you face can distract you from your longer-term objectives. This is not a problem in itself as you have to deal with present demands, but don’t do so without considering and agreeing to the implications on your roadmap.
Regardless of your priorities, there are some fundamental prerequisites in IAM, like reliable 'source of truth' HR data. Understanding what you want to achieve and when will help you to make progress in the correct order for your organisation.
In reality, real value can only be delivered when multiple interdependent factors mature in parallel. These are:
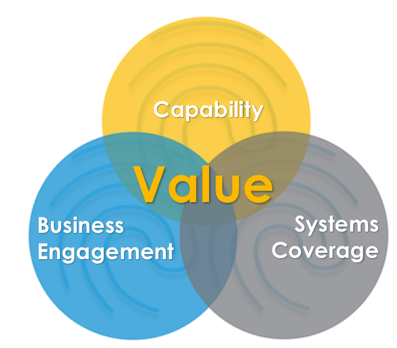
- Capability - The functions and business processes you have enabled
- Systems Coverage - The systems you have on-boarded
- Business Engagement - The departments that are using the capabilities
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
- Capability
IAM capability can generally be split into two categories based on what type of value they primarily deliver - control or efficiency. Consider what your main concerns are and use these to prioritise capability
- Capability
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
If you’re essentially trying to address security or compliance worries, consider prioritising some of the following:
- Leavers - Automatically identify leavers and remove their systems access
- Certification - Review users existing access regularly and at key lifecycle events, e.g when a user changes role
- Reconciliation - Identify and remediate unauthorised changes to access
- Segregation of duties - Identify and enforce which combinations of access can and cannot be held by a user
If however your objectives are more focused on improving efficiency and user experience, consider prioritising:
- Birth-right provisioning - Identify new starters and grant them basic access
- Automated fulfilment - Automate the back end changes necessary to fulfil any access change
- Role-Based Access Control (RBAC) - Group common access into easy to understand business-aligned roles that can be requested or automatically assigned based on HR data
- Access request - Give your users and managers the ability to self-serve access request and approval. Combined with RBAC and automated fulfilment, this can deliver huge experience and efficiency benefits
Of course, security and compliance capabilities will offer some efficiency benefits and vice versa. Justify your approach by considering what you want to improve and which capabilities deliver best against these objectives.
Systems coverage
A set of great capabilities that only affect a small number of systems are not going to deliver many benefits. For the biggest gains, you need to onboard systems, but don’t underestimate how challenging and time-consuming this is. It’s unrealistic and not financially viable to onboard all systems, and certainly not to automate fulfilment on every system. Establish a prioritisation approach based on the value your organisation places on these systems (criticality and sensitivity) but also consider the number and turnover of users on the system and the technical complexity of discovery and onboarding. These factors considered together will allow you to prioritise the systems that are most important but balanced against your cost/benefit considerations.
A set of mature IAM capabilities that affect a good range of systems is a great place to be. However, unless the business is using these capabilities, your value equation will remain incomplete. As with systems, it’s important to achieve adequate coverage across the organisation, but indeed we can’t please all of the people all of the time.
Focus your business engagement in the largest departments with the most users, or high profile areas that will advocate the services to others. Once the big departments are happy the smaller areas will likely follow suit. Also, look to identify a friendly smaller department as a testbed where you can work collaboratively to develop and tune the services before wider rollout. Giving a smaller area influence beyond what they normally enjoy and an early adopter status can generate a productive relationship that benefits both parties.

IAM strategy and implementation experts at Savanti can guide you through the process of developing and executing an IAM strategy. Savanti have a team of experienced IAM specialists who have developed a proven delivery framework and will guide you through all the areas that need to be considered, showing you how to prioritise and address these or lead your whole programme for you.
If you need support with your IAM journey, please get in touch info@savanti.co.uk or visit our website: www.savanti.co.uk
For more information about Savanti's IAM service, please provide your details below:










