Protecting Your Digital Infrastructure
Written by Ryan Perrin, Senior Security Consultant for Savanti, part of FSP

Savanti are proud of their trusted cyber security partnerships with some of the world’s top cloud service providers. Combined with our depth of knowledge in leading-edge and emerging technologies this is a powerful combination which will bring you the scope, agility and flexibility to make your aspirations a reality.
Introduction
In a world where cyber threats pose a relentless and significant risk to both businesses and individuals, Microsoft Sentinel emerges as a cloud-native security solution, offering unparalleled insight and visibility to defend corporate environments from these threats.
What exactly is Microsoft Sentinel, and how does it protect against cyber threats? This post will explain the key features and benefits of Microsoft Sentinel as a tool in your cyber security arsenal.
What is Microsoft Sentinel?
Microsoft Sentinel is a cloud-native platform combining SIEM (Security Information and Event Management) and SOAR (Security Orchestration, Automation, and Response).
It’s designed to provide a seamless security solution for both cloud and on-premises environments, offering a unified interface for monitoring, detecting, and responding to cyber security threats.
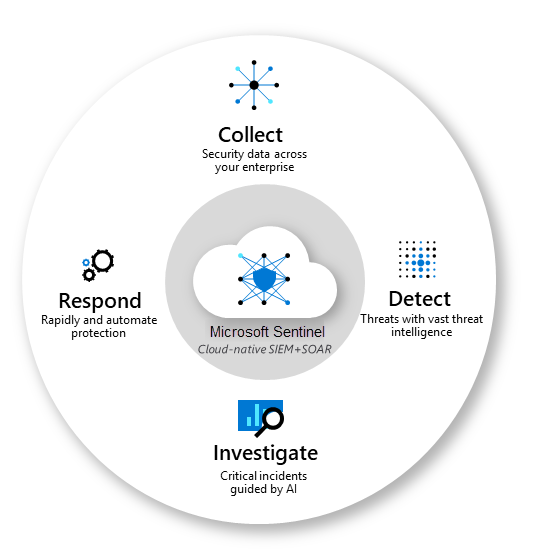
Source: https://learn.microsoft.com/en-us/azure/sentinel/media/overview/core-capabilities.png
Understanding SIEM and SOAR
As a SIEM solution, Microsoft Sentinel collects and analyses security data from various sources such as operating systems, applications, servers, and network equipment. This centralised approach is key for detecting threats, managing compliance, and handling security incidents.
In its SOAR role, Microsoft Sentinel automates incident response. It streamlines workflows and integrates with other security tools to automate investigation and remediation tasks. This automation helps security teams respond to alerts faster and more efficiently.
Microsoft Sentinel serves as a comprehensive tool for monitoring, detecting, and responding to security threats in a unified, cloud-based environment.
The Benefits of a Cloud-Native SIEM
Scalability: One of the most significant benefits of a cloud-native SIEM is its ability to scale with the needs of your business. Microsoft Sentinel’s cloud-native structure allows it to scale with your organisation. As data volume and security demands grow, Sentinel manages this without additional physical infrastructure, ensuring that security measures grow with your company.
Cost-Effectiveness: Microsoft Sentinel offers a pay-as-you-go model, eliminating the need for large upfront investments in hardware and software common in traditional SIEM solutions. This approach reduces long-term maintenance and upgrade costs and allows organizations to save on expenses related to system maintenance, power, cooling, and space due to Microsoft’s management of the underlying infrastructure.
Speed and Agility: Deploying Microsoft Sentinel is typically faster than setting up an on-premises SIEM system. There’s no hardware to procure and configure, and software installation and patching are handled by Microsoft. This means you can go from purchase to protection much quicker. Moreover, updates and new features are rolled out by Microsoft automatically, ensuring that you always have the latest security capabilities without the downtime typically associated with manual updates.
Advanced Security Features: Being built on the cloud, Microsoft Sentinel can leverage advanced security features that may be more challenging to implement in an on-premises environment. These include machine learning and artificial intelligence capabilities for anomaly detection and threat intelligence insights that are continuously updated.
Flexible Data Storage and Retention: Cloud-native SIEM solutions offer flexible options for data storage and retention. With Microsoft Sentinel, you can adjust your data retention policies to meet your organisation’s needs and compliance requirements. This flexibility allows you to store vast amounts of data without worrying about the physical limitations of on-premises hardware.
High Availability and Disaster Recovery: Microsoft Sentinel benefits from the high availability and disaster recovery capabilities built into the Azure cloud platform. Your SIEM infrastructure can be resilient to outages and disruptions, with data replicated across multiple geographic locations. This ensures continuity of security operations and preserves critical security data.
Core Components of Microsoft Sentinel
Data Connectors integrate Microsoft Sentinel with your data sources, enabling the ingestion of data from Azure services, Microsoft 365, other cloud services, and on-premises servers. Connectors are designed to collect logs and events from designated sources, formatting and enriching the data for subsequent analysis. Sentinel’s extensive range of connectors allows for the consolidation of data from various points in your IT infrastructure, offering a unified security overview.
Analytics Rules in Microsoft Sentinel detect potential security threats by analysing incoming data. These rules are set based on threat patterns, anomalies, or compliance needs. Custom rules can be created, or users can implement Microsoft’s pre-defined templates, which draw from current threat intelligence. Triggered rules generate alerts for security analysts to examine, helping to identify important issues within large data sets.
Incidents in Microsoft Sentinel aggregate related alerts that could signify a complex threat or breach. They organise multiple alerts into a single view, aiding teams in prioritising investigations. Incidents provide essential data, including impact, timelines, and affected resources, to enable a prompt, coordinated response.
Playbooks are automated sequences in Microsoft Sentinel that address security incidents. As part of the SOAR (Security Orchestration, Automated Response) capabilities, they execute actions ranging from notifications to isolating compromised systems. By automating routine tasks, playbooks free up security teams to concentrate on higher-level analysis and decision-making.
Workbooks provide customisable dashboards within Microsoft Sentinel that enable users to visualise and analyse the data. They can be used to create interactive reports, track security metrics, and monitor the status of alerts and incidents. Workbooks are highly flexible, allowing users to tailor the layout and data presented to meet their specific needs. They are essential tools for ongoing monitoring and for gaining insights into trends and patterns over time.
Threat Intelligence feeds are incorporated into Microsoft Sentinel, aiding in the detection of recognised malicious indicators, including IP addresses, URLs, and file hashes. This intelligence is used to enrich alerts, providing context that can accelerate investigation and response. Users can also integrate their own threat intelligence feeds or use the built-in Microsoft Threat Intelligence for a more robust threat detection capability.
KQL (Kusto Query Language) is the query language for Microsoft Sentinel, enabling detailed searches and data analysis. It allows for complex queries to isolate events, discern trends, and deeply analyse security data. KQL’s range of functions and operators makes it indispensable for detailed threat hunting and security investigations.
How Microsoft Sentinel Works
Understanding the operational flow of Microsoft Sentinel is crucial for effectively utilising its capabilities, here’s how it typically works:
Data Ingestion: The process begins with data ingestion. Microsoft Sentinel uses connectors to pull in data from various sources, including other Azure services, Microsoft 365, and third-party solutions. This data can include logs from firewalls, event management systems, and endpoint security solutions, among others.
Threat Detection: Once data is ingested, Sentinel applies its analytics rules to the data stream. These rules are powered by Microsoft’s threat intelligence and machine learning algorithms to identify suspicious activities and potential threats. Users can also create custom rules tailored to their organisation’s specific security concerns.
Alerts and Incidents: When a threat is detected, Sentinel generates alerts. These alerts can be correlated with other related alerts to form incidents. This correlation helps security teams to focus on the broader context of an attack rather than isolated events.
Investigation and Response: Security professionals can then investigate incidents within Sentinel’s interface, using tools like the investigation graph to visualise relationships between entities and events. For identified threats, Sentinel’s SOAR capabilities allow for automated responses, such as isolating compromised machines or revoking user access, through predefined playbooks.
Continuous Learning: Sentinel is not static; it learns and adapts. The system refines its detection capabilities over time, using feedback from security analysts and ongoing machine learning to improve the accuracy of alerts and reduce false positives.
Proactive Threat Hunting: Beyond reactive threat detection, Sentinel enables proactive threat hunting. Security teams can use the Kusto Query Language (KQL) to create sophisticated queries that search through historical data for signs of previously undetected threats.
Reporting and Compliance: Finally, Sentinel provides comprehensive reporting tools and workbooks that help organisations meet compliance requirements and maintain oversight of their security operations.
Microsoft Sentinel in Action
To illustrate Microsoft Sentinel’s capabilities, consider a scenario where an organisation faces a sophisticated phishing attack:
Detection: Sentinel’s analytics rules detect an unusual login attempt from a location never before used by the user. Simultaneously, a suspicious email attachment is opened by several employees, triggering another set of alerts.
Automation: A playbook is automatically initiated, which isolates the affected users’ accounts and endpoints, preventing further spread of the potential threat.
Investigation: Security analysts are alerted and begin an investigation using the rich data provided by Sentinel, including user activities, login locations, and related events.
Resolution: After identifying the phishing email source, analysts use Sentinel to track the attack’s spread across the network and remediate the issue. The playbook also reverses the isolation for verified safe accounts and endpoints.
Conclusion
Microsoft Sentinel stands out as a comprehensive security solution, combining the strengths of SIEM (Security Information and Event Management) and SOAR (Security Orchestration, Automation, and Response) within a cloud-native framework.
As a SIEM, it excels in aggregating security data from across your organisations environment, providing advanced analytics to detect threats.
As a SOAR, it streamlines incident response with automated workflows.
The core components, including data connectors, analytics rules, incidents, playbooks, and the user-friendly dashboards, form the backbone of Sentinel’s robust security infrastructure.
This integration not only simplifies the complex landscape of cyber security but also enhances an organisation’s ability to respond to threats swiftly and effectively.
Savanti’s Microsoft services can provide you with an experienced team of experts dedicated to supporting you to deliver both tactical and strategic services.
Please visit the chat function on our website or fill in the below details if you would like more information on how we can support you on your journey with Microsoft technologies.
Feature image used: by Gerd Altmann from Pixabay











